June 29, 2017
On Tuesday, cyber criminals launched yet another ransomware attack targeting businesses and government agencies across the globe. This virus, dubbed the “Petya,” “NotPetya,” “Petna,” or “Petrwrap” virus, exploits the “Eternal Blue” vulnerability in the Microsoft Windows system — the same weakness recently targeted by the WannaCry virus. Petya also tries to sidestep security patches by launching attacks through other avenues. If successful, the ransomware spreads rapidly across the network and demands $300, paid in Bitcoin, to save the computer files from eternal encryption.
Here are a few things you need to know:
- Several major antivirus companies claim they are now fully updated to protect against Petya, so be sure to check to make sure your anti-virus systems are running on all cylinders and that all recent Microsoft updates have been installed on your system.
- According to one online security expert, Petya ransomware reportedly infects the computer and then waits for one hour to reboot the machine. During this process, the following message may appear during the encryption process:
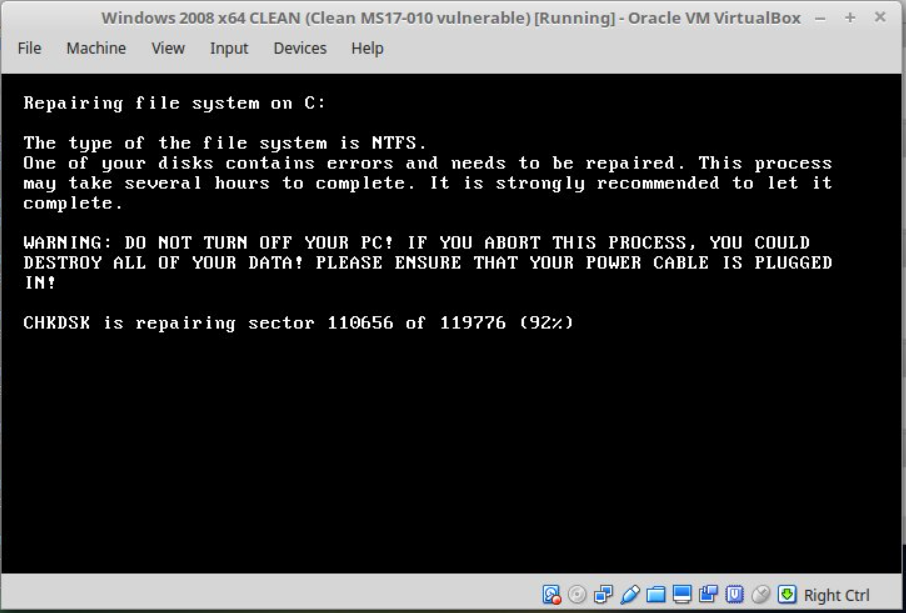
If you see this message on your computer, the expert reports that you can immediately turn the system off to stop the encryption cycle and preserve the ability to somehow rescue files off the system. News outlets are also reporting about a “localized kill switch” for the virus that involves changing a single filename that tricks the malware into shutting down.
Take a look at the strategic tips outlined in Hancock Daniel’s WannaCry Ransomware Alert. Those measures and others will help healthcare providers and other businesses to limit their exposure to the virus and other cyber threats lurking on the worldwide web.
If you have questions or need assistance regarding these strategies or other cyber security and privacy issues, please contact Hancock Daniel’s Cybersecurity team.
The information contained in this advisory is for general educational purposes only. It is presented with the understanding that neither the author nor Hancock, Daniel, Johnson & Nagle, PC, is offering any legal or other professional services. Since the law in many areas is complex and can change rapidly, this information may not apply to a given factual situation and can become outdated. Individuals desiring legal advice should consult legal counsel for up-to-date and fact-specific advice. Under no circumstances will the author or Hancock, Daniel, Johnson & Nagle, PC be liable for any direct, indirect, or consequential damages resulting from the use of this material.

